Home office security - cyber attacks and how to protect yourself
While working from home once was an exception, now it is omnipresent due to COVID-19 pandemic measures. Importantly, companies’ cyber security suffers from this major transition to home offices. There is often a lack of IT and security know-how at home. The same is true for remote working.
We will explain the different types of cyberattacks, how to ensure maximum security in Microsoft Teams, and what measures you should take to achieve optimal home office and mobile working security.
Identify home office security issues
Moving to a home office comes with many cyber security dangers. The seriousness of this problem is shown in a study by the German Economic Institute: damages due to cyberattacks in 2021 increased by more than €120 billion compared to 2019, to €223.5 billion. Damage caused by cyberattacks in mobile work accounts more than doubled in two years, accounting for a significant share of this total, at €52.5 billion.
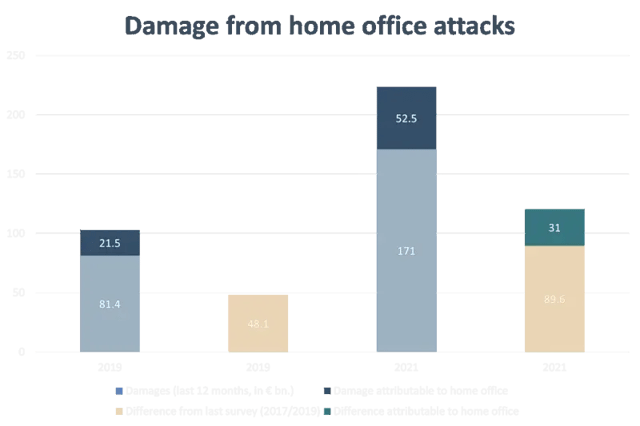 Source: Institut der deutschen Wirtschaft Köln e.V. / German Economics Institute
Source: Institut der deutschen Wirtschaft Köln e.V. / German Economics Institute
Before concrete measures can be taken, you should first get an overview of the status quo of your IT security in the home office. A survey by the BSI shows that even basic technical security measures such as using a VPN or multi-factor authentication are often not implemented.
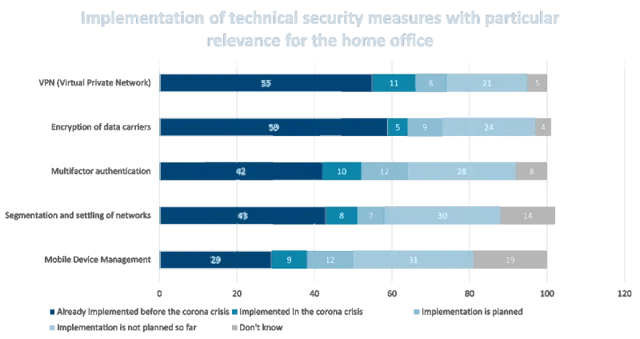 Source: Bundesamt für Sicherheit in der Informationstechnik / Federal Office for Information Security
Source: Bundesamt für Sicherheit in der Informationstechnik / Federal Office for Information Security
With regard to organizational security measures for the home office, the German Federal Office for Information Security (BSI) survey shows that action is still clearly needed. Only security training for employees is frequently implemented. But coherent, robust security measures - like emergency drills, dedicated IT security departments, or IT security strategies - are frequently missed.
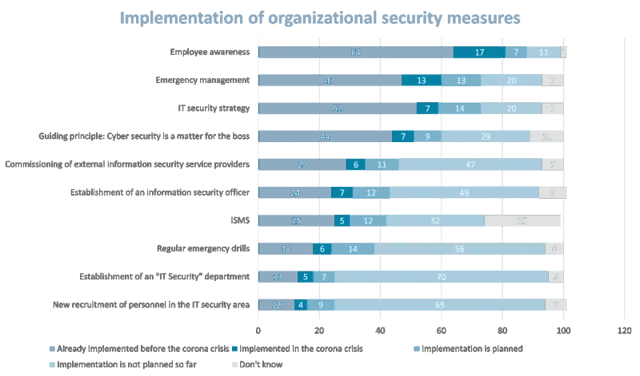 Source: Bundesamt für Sicherheit in der Informationstechnik / Federal Office for Information Security
Source: Bundesamt für Sicherheit in der Informationstechnik / Federal Office for Information Security
Types of cyber attacks related to remote work
To increase awareness of cybersecurity in the home office, it helps to focus on the most common types of cyber attacks affecting home office and mobile working.
As a general rule, always question transactions and data transfers critically, make sure you have a secure IT foundation, and if in doubt, check again. You should always keep data security in the home office in mind.
Phishing
In phishing, fraudsters use e-mails, fake websites, and other methods to try to obtain sensitive data or get you to transfer money. This is usually done by imitating known persons (team members, managers, business partners) or trustworthy service providers (banks, companies with which a business relationship exists, or government offices) to exploit a victim’s trust. Phishing e-mails and websites can be visually identical to the originals, so extra caution is required.
To protect yourself from phishing attacks, you should always treat e-mails, attachments, links, and websites with suspicion.
- If in doubt, seek personal contact. However, you should never use the contact data from the e-mail because they can be falsified. It is better to use contact details in your own address book or search online for official contact details.
- When receiving invoices, check whether the service has actually been provided. Also, double-check with the vendor about any payment instructions like bank account information - but as a separate phone call or email, not a reply to what you have received.
- Never pass on login data to anyone for any reason, not even to someone claiming to work for your IT department. Your IT department will never ask you to do that.
- Check email addresses and links carefully. Often a known sender’s name is used but the email address is different. Pay close attention to the part of the address after the @ - it should exactly match the address you know is valid. If it does not, do not respond or open any attachments, instead, contact your IT department.
- You should never open attachments in e-mails from unknown addresses.
- And when in doubt, contact your IT department.
Spearphishing: "CEO fraud"
Normal phishing attacks usually involve generic emails sent to many victims. Spear phishing entails targeted attacks. Perpetrators research the victim to craft their emails with detailed, accurate, credible information. In the case of a spearphishing CEO fraud, the attacker imitates the victim’s superior who urges them - often under time pressure - to pass on information or even to transfer sums of money. Detailed imitation makes CEO fraud attacks particularly difficult to detect.
In general, the safeguards against phishing attacks apply here as well. Try to contact your supervisor personally to clarify the situation. Often, CEO fraud scammers try to create a pressure situation and signal that the supervisor will not be available. Especially when it comes to home office security, it is therefore important to ensure that supervisors' schedules are traceable. In addition, an approval process should be established before payments are made, and awareness training should be provided to employees.
Man-in-the-middle
In man-in-the-middle attacks, a fraudster acts as an intermediary between two communication parties without their knowledge. In doing so, they try to learn important, confidential information such as passwords, login data, or company internals. This type of attack is particularly dangerous in home offices where IT security is often not optimal.
To avoid man-in-the-middle attacks, you should not use public WiFi / (W)LAN unless you connect to a VPN first. This is especially important when working on the move. In addition, your system should always be up to date because man-in-the-middle attacks often exploit security gaps. For websites, you should look for SSL or TLS encryption, which encrypts the communication between the server and the visitor. Two-factor authentication can also help, as this can prevent unauthorized logins even if login data has been tapped.
Malware
Malware are computer viruses that can have a wide variety of effects. For example, data can be locked and a "ransom" demanded it (ransomware) or passwords and login data can be spied on (spyware). In terms of home office security, malware is a major problem because often too few security precautions are taken. The range of malware attacks is enormous, so the more you do for home office security, the safer you are.
Malware is mainly spread via email (as a link or attachment), so the same caution applies here as with phishing attacks. The most effective mitigation here is to raise awareness through training on cybersecurity in the home office. If an attack is nevertheless successful, regular backups are the most effective means of reversing it. Especially in the home office backups are often lacking, however.
Measures to increase home office security
Now that we have covered the most common cyberattacks and methods to increase telecommuting security, we want to share how to work securely from home with some general tips. We will focus on Microsoft Teams, which serves as the foundation for many people's mobile and home office work.
Home office work and security in Microsoft Teams
Since the switch to a Modern Workplace, Microsoft Teams has served many companies as a hub for collaboration. So it is extremely important for home office security to understand Microsoft Teams and its use in detail.
Microsoft Teams includes a high level of security from a technical point of view. Read more about that in our article on Microsoft Information Protection. All data in Teams is encrypted, before it is transmitted and secured. Enforced 2-factor authentication ensures hightened login security. Nevertheless, to ensure maximum home office security in Microsoft Teams, you should take some additional measures.
The most important measure for security in Microsoft Teams is the sensible division into smaller teams. This can ensure that only authorized people have access to the data relevant to them, since everyone involved in the team is known to the "owner" of the team. Permissions should also be adjusted depending on the user group (owner, members, guests).
If you frequently collaborate in Microsoft Teams with customers or business partners, it may make sense to create two teams: an internal team in which you actively work on documents and in which only employees are members, and an external team in which your customers and business partners are also members. This increases information security because it facilitates appropriate access to data and external users are only provided with the data that you specifically release to them.
Another option to increase security in a flexible workplace with Microsoft Teams is to additionally protect important documents with passwords. However, these passwords should not be communicated via Teams itself in order to make interception via man-in-the-middle or malware attacks more difficult. You can find more helpful tips and information about Microsoft Teams in our Microsoft Teams guide.
General tips for home office security
In general, keep a few things in mind when it comes to home office and mobile working security. The most important rule: clarify all security issues with your IT department. Shadow IT, i.e. programs, services or devices that employees use with company data without clarifying this beforehand, pose a major risk. Employees should get permission to use them and, ideally, have devices set up by IT experts. The IT department should also provide a checklist for the use of private devices and services.
Whenever working outside the office, use a VPN connection, even when connecting to the secure company network.
Working securely is easy
Working securely when working remotely is easy - at home or on the road - if you have the right tools, processes, behaviors, and security mindset. The IT team must ensure systems are secure and only securely accessible. All employees, from CEO all the way to temporary intern, must understand and practice good cyber security hygiene. Transparency about how to handle security risks and breaches is crucial. We highlight many additional measures around data protection in the home office in our article on the Modern Workplace.
You May Also Like
Related articles

Modernizing legacy software: Initiate the change

Microsoft Ignite: Changes in 2021


