Microsoft Cloud Security: insights into security in the cloud
Are you using or thinking about using cloud services? If so, you've probably wondered how to keep cloud documents safe from cyber attacks. As businesses and individuals rely more and more on cloud solutions, the security of the data and applications stored in the cloud is becoming an increasing priority.
As one of the leading providers of cloud services, Microsoft has made these challenges a priority and is continuously developing solutions to ensure security in the cloud. In this blog post, we will take a deep dive into the world of Microsoft Cloud Security. We will explore the various components and features of this suite to understand how it helps organizations protect their cloud resources from threats.
- The importance of security in the cloud
- What is Microsoft Cloud Security?
- What makes up Microsoft Cloud Security?
- How secure is the Microsoft Cloud?
- empower® in the Microsoft Cloud
The importance of security in the cloud
The benefits of using cloud services are many: scalability, efficiency, low cost, and anywhere access. At the same time, cloud storage in the cloud presents a new set of challenges, especially when it comes to security.
Organizations store a variety of sensitive data in the cloud, including customer data, trade secrets, and financial information. The security of this data is paramount to ensure its integrity and confidentiality. Many industries and countries have strict regulations and compliance requirements related to data protection. When this is the case, organizations must ensure that they meet certain requirements to avoid penalties and legal consequences.
The threat landscape is constantly changing, and cybercriminals are becoming more sophisticated. Organizations are constantly exposed to attacks such as ransomware, phishing, and denial-of-service (DDOS) attacks. A robust cloud security strategy is essential to defend against these threats. With the advent of remote working and distributed teams, access to corporate data from anywhere has become a necessity. This increases the attack surface.
Cloud security plays an important role in ensuring business continuity. The availability of data and applications in the cloud, even in the event of a disruption or disaster, is critical. A data leak or security breach can not only result in financial loss but can also severely damage a company's reputation.

Companies that offer strong cloud security can use it as a competitive advantage. Customers and business partners are more likely to work with companies that take the security of their data seriously.
What is Microsoft Cloud Security?
The Microsoft Cloud Security Suite is a comprehensive set of tools and services for protecting your data, applications, and infrastructure in the cloud. This suite of security products and tools provides organizations with a robust security platform to protect their cloud workloads and resources from threats while meeting compliance requirements. The solutions enable real-time detection of threats and attacks in your cloud environment. This enables rapid response to security incidents.
Key benefits of Microsoft Cloud Security include:
- more security in the cloud
- defend against emerging threats
- control access to critical cloud applications and resources
- secure every step of the development lifecycle
What makes up Microsoft Cloud Security?
The Microsoft Cloud Security Suite consists of 6 different applications, each of which is described in more detail below.
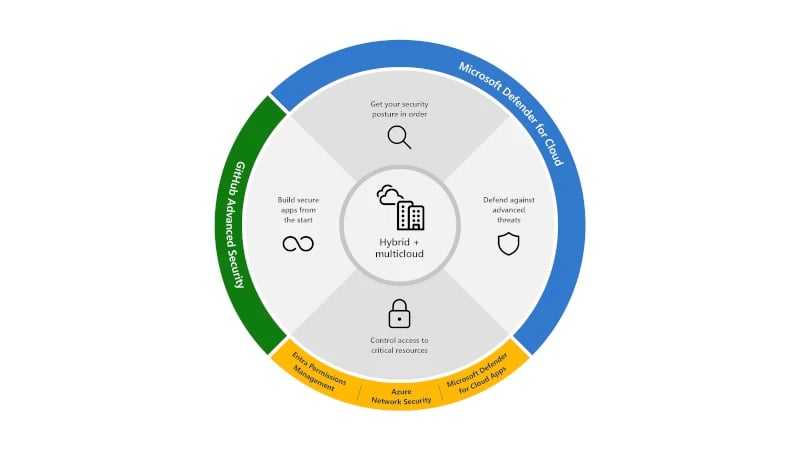
Source: Microsoft
Microsoft Defender for Clouds
Microsoft Defender for Cloud is a centralized management solution that provides security controls and tools to proactively protect against emerging threats in an ever-changing threat landscape. Standard policies provide a secure foundation. Custom policies can be built on top to meet your business needs. All Azure and Office 365 services are automatically integrated at deployment. They are then continuously assessed to provide recommendations for improving security.
Microsoft Defender for Cloud helps you mitigate security risks and prevent threats through contextual security management. If they do occur, you can detect them early and respond accordingly. Microsoft Defender for Cloud also unifies your DevOps.
Microsoft Defender for Cloud provides Cloud Security Posture Management (CSPM) and Cloud Workload Protection (CWP) to improve the security of single, multi-, and hybrid cloud environments and services. It reduces the operational burden on security teams by consolidating endpoint protection, threat protection, and analytics into a single pane of glass. Integrates with other Azure services such as Azure Policy, Azure Monitor, and Azure Cloud App Security for robust and comprehensive cloud security.
Microsoft Defender for Cloud Apps
Microsoft Defender for Cloud Apps is a Cloud Access Security Broker (CASB). It supports multiple deployment modes, including log collection, API connectors, and reverse proxy. The CASB provides comprehensive visibility, data transfer control, and advanced analytics to detect and defend against cyber threats for all SaaS applications.

In addition, Microsoft Defender for Cloud Apps provides additional capabilities beyond traditional CASB. This enhances application security and protects against malicious cloud apps. The combination of SaaS security management, data loss prevention (DLP), app-to-app protection, and integrated threat protection provides comprehensive protection for your applications.
GitHub Advanced Security
GitHub Advanced Security is a powerful security platform integrated built into GitHub that can help organizations of all sizes protect their code base and secure their software development process. It does this by incorporating DevSecOps principles.
In summary, GitHub Advanced Security can do the following things:
- security feedback with every Git push
- fast response to supply chain vulnerabilities
- no more secrets in the source code
- builds a secure foundation
Microsoft Entra Permissions Management
Microsoft Entra Permissions Management is a cloud infrastructure permissions management solution that provides a unified platform to discover, remediate, and continuously monitor permissions for all identities - both users and workloads - across Amazon Web Services, Microsoft Azure, and Google Cloud to strengthen your Zero Trust security and protect your multi-cloud environment.
Get a detailed view into every action taken by every person on every resource in the cloud. Unused and risky privileges are automatically identified. This allows you to enforce least privilege in the cloud and grant additional privileges as needed. Highly accurate machine-learning alerts to detect deviations and detailed reports allow you to continuously monitor your infrastructure for future permission extensions.
Azure Network Security
You get a detailed view of every action taken by every person on every resource, and Microsoft Azure is one of the leading cloud service providers. It offers several features to help organizations secure their virtual networks. One security mechanism is Azure Network Security Groups (NSGs). NSGs play an important role in controlling inbound and outbound traffic to Azure resources, ensuring a secure and manageable cloud environment. They have control over traffic to and from Azure resources, such as subnets and network interfaces connected to VMs. They consist of inbound and outbound security rules that allow or deny network traffic based on characteristics such as IP address, port, and protocol across the cloud. Unused and risky privileges are automatically identified. This allows you to enforce least privilege in the cloud and grant additional privileges as needed. Highly accurate machine-learning alerts to detect outliers and detailed reporting allow you to continuously monitor your infrastructure for future privilege expansion.
Each Azure subscription can have multiple NSGs. These can be associated with different Azure resources within a resource group. The rules of an NSG can be customized to meet your business needs to ensure a secure Azure virtual network (VNet) and effective Azure security.
Microsoft Defender External Attack Surface Management
Microsoft Defender EASM uses crawling technology, part of the Microsoft infrastructure, to discover resources connected to the online infrastructure. The technology actively scans to gain more information and identify vulnerabilities in cloud, SaaS, and IaaS resources.
By combining Extended Detection and Response (XDR) and Security Information and Event Management (SIEM), you can put yourself in the attacker's shoes and effectively protect your digital assets.
How secure is the Microsoft Cloud?
Cloud solutions are generally more secure than on-premises solutions because they tend to have more resources dedicated to maintenance. However, cloud solutions are not 100% secure. At the same time, the potential risks of Microsoft cloud security are not unique to Microsoft:
- blob hunting data collection
- credential theft
- insider threats with existing privileges
- leaks
- compromised third parties with privileged credentials
- access token abuse
- shadow IT
Microsoft has very high security standards. In addition, Microsoft has many security-related certificates. As shown in the following figure, Microsoft alone has 18 compliance standards that apply worldwide.

In addition, there are more than 50 certifications for specific regions and more than 35 compliance offerings for specific industries, such as government, education, and manufacturing.
A question many people ask themselves: Who is liable in the event of a security breach? This is where the shared responsibility model comes in. It defines the security obligations of a cloud provider and its users in the context of cloud security.
When an organization operates and manages its own IT infrastructure in its own data center, it and its IT staff, managers, and employees are responsible for the security of that infrastructure and the applications and data that run on it. By moving to a cloud model, an organization transfers some, but not all, of these IT security responsibilities to its cloud provider. Both parties - the cloud provider and the cloud user - are responsible for different aspects of security and must work together to ensure complete coverage.
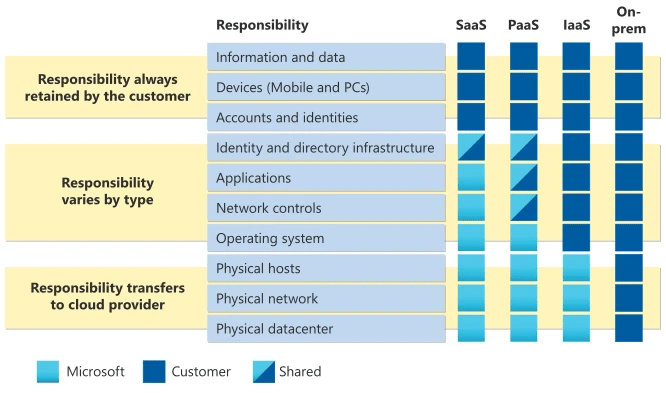 Source: Microsoft Learn
Source: Microsoft Learn
empower® in the Microsoft Cloud
The empower® backend and web applications are also hosted in the cloud - on Microsoft Azure resources, including Azure VMs and Azure SQL. empower® thus benefits from the high security standards of the Microsoft cloud. For additional security, empower is ISO27001 certified for information security management, meeting proven international standards. The certificate specifies the development, deployment, and support of technologies for marketing and sales management.
Have a question about the empower® software suite? Contact us - we are here to help.
You May Also Like
Related articles

Data security with Microsoft Information Protection

Leverage your IT investments with the Microsoft Cloud


